Malware and viruses may sound like spooky relics of the early 2000s, but these insidious threats haven’t disappeared. In fact, one 2024 study found that around 6% of smartphones were infected with malware. That’s around 295 million devices worldwide.
Despite advancements in mobile security like biometric authentication and app verification, hackers are still finding ways to infiltrate phones, often through phishing or social engineering attacks, rogue apps, and software vulnerabilities. These intrusions can result in financial fraud or even identity theft.
In this article, we’ll teach you how phones get hacked, how to tell if yours has been exposed, and different ways to unhack your phone.
How does someone hack your phone?
Attackers can hack your phone in several ways: for starters, they can trick you into clicking a fake link or downloading a malicious attachment, intercept your data on unsecured networks, or exploit app or system vulnerabilities. This is especially true if you’ve taken steps that compromise your device’s built-in protections, like jailbreaking your iPhone or disabling Gatekeeper to install an unverified app.
Here’s a closer look at some common ways phones get hacked:
- You downloaded a malicious app: Some apps, especially from unofficial sources, contain hidden malware that can steal your data or track your activity.
- You clicked on a smishing link: A fake text message may include a link that installs malware or steals login credentials when interacting with it.
- You opened an attachment: Malicious files sent via email, messaging apps, or AirDrop can compromise your device once opened.
- A drive-by download exploits vulnerabilities: In some cases, visiting a compromised website can install malware on your phone, even if you don’t open an infected link or file.
- You shared information with someone you shouldn’t: Social engineers and fraudsters can trick you into revealing private data by impersonating trusted entities like customer support.
- You connected to an unsafe Wi-Fi network: Hackers can intercept your data on public or unsecured networks through man-in-the-middle attacks.
- You reused passwords across accounts: If one account, like your email, is breached, and you use the same password everywhere on the internet, attackers could potentially hack your phone by accessing synced apps, cloud backups, or linked services, giving them access to your device and personal data.
- You’re targeted by a SIM swap attack: If a social engineer convinces your mobile carrier to switch your number to a new SIM in a SIM swap attack, they could get access to your calls, texts, and two-factor authentication (2FA) codes.
12 signs that your phone is hacked
If your phone performs poorly, you can’t get into your accounts, battery and data usage are high, or you notice other odd behavior, your phone might be under attack. Learn more about the red flags you’ll likely encounter.
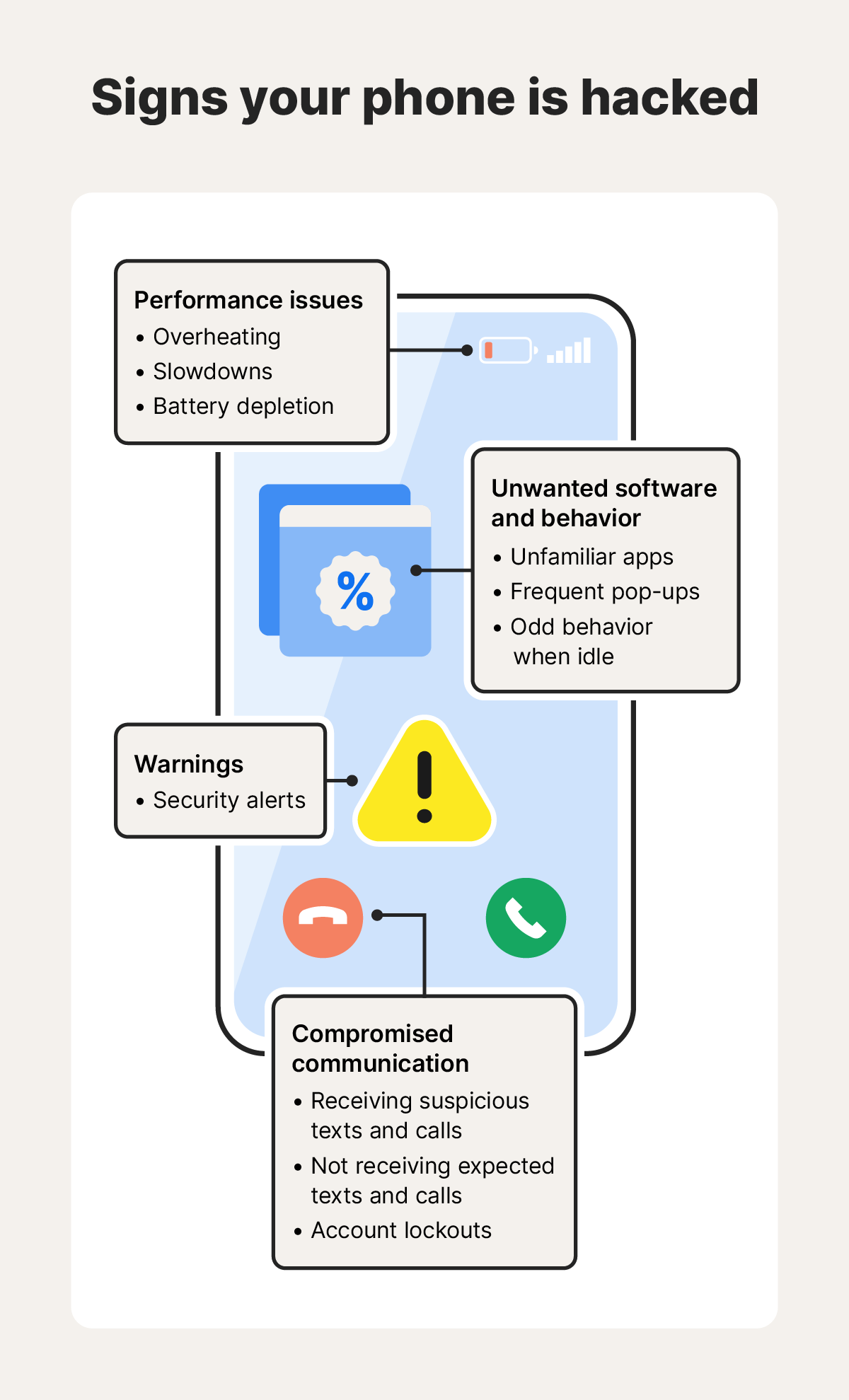

1. Your phone is hot
Malware runs in the background so it can continuously collect and transmit data to attackers. This requires a lot of processing power, and can make your phone feel warm to the touch, even when you’re not using it.
2. Your phone is slow or crashes frequently
Since apps running in the background use up system resources, you may notice apps lagging if there’s not enough memory available. Your phone may also reboot without warning to clear overloaded processes or recover from a crash.
3. The battery is draining quickly
Another side effect of malware consuming excessive processing power is a rapidly draining battery. Processes like constant data transmission and background crypto mining can deplete battery life, since they run continuously and demand high system resources.
4. You’re receiving suspicious texts and calls
You may get two-factor authentication (2FA) codes you didn’t request if someone is trying to access your accounts. This may happen if your email or login credentials are leaked, and a hacker is trying to change your password.
5. You’re not receiving expected texts and calls
Hackers can intercept or reroute your messages and calls by tricking your phone carrier into transferring your number to their device in a SIM swap attack, potentially granting them access to 2FA codes sent to your device via text. If cybercriminals intercept your 2FA codes, they could hack into your digital accounts across the internet and potentially steal your identity.
6. Your contacts get weird messages from you
If a hacker gains control of your phone or SIM card, they may attempt to send phishing links to your friends or contacts or trick them into sending money.
7. Unfamiliar apps appear on your device
If you see apps you don’t remember downloading, they might be spyware or trojans planted to monitor your activity or steal personal data. Some apps may just be pre-installed bloatware from your phone carrier or manufacturer, but generic apps that request too many permissions and run your battery dry could be malicious.
8. You see frequent pop-up ads
Certain types of malware, like adware, bombard your phone with pop-up ads, banners, and notifications, even if you’re not using an app. These infections can make your phone nearly unusable due to the onslaught of interruptions. If you click on a malicious ad or get redirected to an unsafe site, it can also lead to further infections.
9. Your data usage is high
If you’re blowing through your data plan faster than expected, malware might be using your mobile data to communicate with command-and-control servers, upload stolen information, or run hidden processes in the background. To tell, check which apps are using the most data in your settings. Unfamiliar apps you don’t use frequently shouldn’t consume much data; if they do, you could be dealing with malware.
10. You can’t access your accounts
If you try to log into your accounts and can’t, an attacker may have hacked your phone and changed your login credentials. They may have taken over your accounts remotely with a Remote Access Trojan (RAT) or by redirecting your 2FA code to their phone through a SIM swapping attack or with spyware.
11. Your phone behaves oddly
Excessive resource consumption and active spyware use can make your phone go haywire. Apps might launch on their own, and the camera or microphone indicator lights may turn on even when you’re not using your device. If spyware is secretly recording or transmitting audio, you might also hear strange sounds, like static, clicks, or distant voices.
12. Security alerts or warnings appear
If your smartphone is hacked, you may get email alerts or push notifications from your antivirus or mobile security apps notifying you of suspicious activity, unauthorized changes or logins, or unknown devices connected to your phone’s network.
If you want powerful Cyber Safety software that combines identity protection and antivirus, try Norton 360 with LifeLock. It features AI-powered scam detection, spyware defense, and the signature LifeLock identity protection trusted by millions, keeping both your identity and your devices safer from cybercrooks.
How to confirm if your phone is hacked
Certain device behaviors scream “hack,” but sometimes there’s another cause behind the issues. Complete these steps to confirm if your phone is actually infected or if it could be acting buggy due to issues like low storage or outdated software.
- Run a malware scan: If you think somebody hacked your phone, use a trusted malware scanner, like the one included in Norton 360 with LifeLock, to detect and remove any threats.
- Look for unfamiliar apps: Go to your app list in settings and check for any applications you didn’t install. Focus on apps that consume lots of data or battery without explanation: these could be malicious.
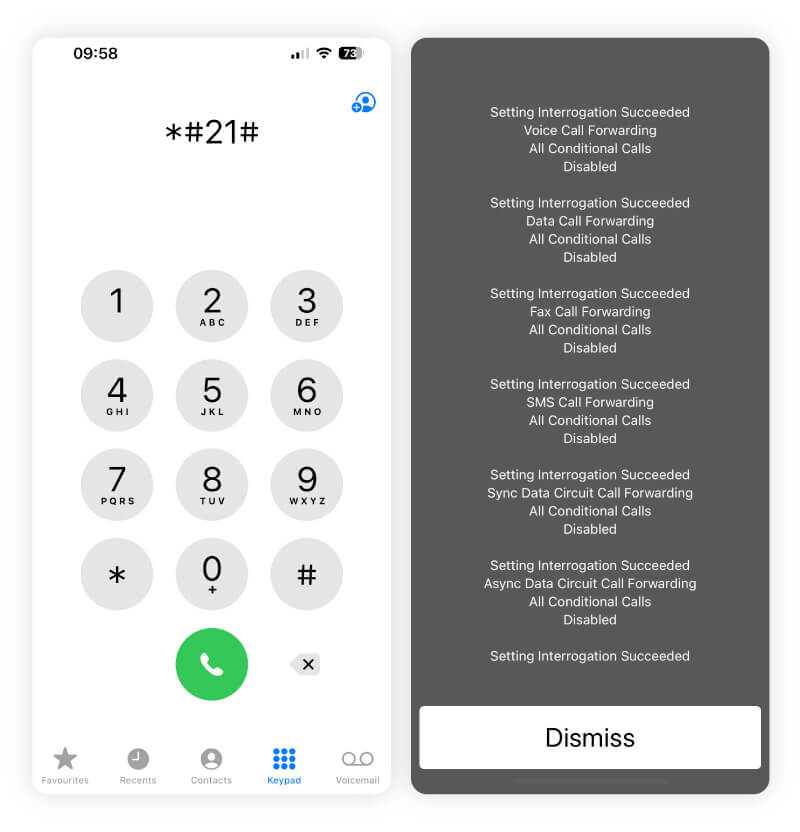
- Dial codes to reveal hidden phone settings: Codes like *#21# or *#62# can tell you if somebody is forwarding your calls or texts on Android or iPhone. In the response you receive after dialing these codes, sections that say “Disabled” or “Not forwarded” indicate call forwarding isn’t set up; any other variation that you didn’t configure could mean someone else has enabled call or message forwarding to intercept your communications.

How do I unhack my phone?
If your phone is hacked, quickly take steps such as disconnecting from networks, backing up essential data, and running a malware scan to regain control and limit data theft. To do this:
- Disconnect from the internet: Disable Wi-Fi and cellular data to prevent malware from communicating with outside servers.
- Backup data: Save only essential files to a secure cloud or external drive to avoid transferring any malware along with your backup.
- Run a malware removal tool: Use a reliable mobile security app to remove any detected threats and clean your system. Norton 360 with LifeLock makes this process simple.
If the malware holds on after this, you can try to manually rid yourself of the infection by deleting unnecessary or suspicious apps, clearing your browser cache, and removing unfamiliar devices linked to your accounts. If all else fails, consult a cybersecurity expert or factory reset your device.
How to protect your phone from hackers in the future
Good habits like installing software updates and avoiding suspicious downloads can go a long way in protecting your personal data and device from future attacks. Here’s a closer look at what you should do to defend your phone from attackers:
- Install software updates: App and operating system updates patch security vulnerabilities that can be exploited if left unchecked. Turn on automatic updates for your phone and apps to maximize your protection.
- Only download apps from reputable marketplaces: Avoid third-party app stores, and always review an app’s permissions before installing.
- Don’t jailbreak your phone: While jailbreaking a phone gives you more customization options, it also disables built-in security features that guard against malware.
- Lock your SIM: Set up a SIM PIN (a four-digit number) to prevent attackers from inserting your SIM card into their phone or using it without permission.
- Use an ad blocker: Stop malicious ads and redirects by enabling ad-blocking extensions.
- Set up two-factor authentication: For stronger security, protect your accounts with 2FA or MFA, preferably using an authenticator app rather than SMS codes.
- Update your passwords: Guard your online accounts with strong and unique passwords. This helps prevent attackers from hacking your phone in the future by reducing the risk of credential stuffing and unauthorized access through reused or weak passwords.
Monitor your phone for suspicious activity
After you’ve taken steps to boot hackers from your phone, monitor for signs of financial and identity theft. LifeLock offers tools to help you monitor for data breaches, new accounts opened in your name, and suspicious movement on your credit report, alerting you if you’re at risk.
And, if your identity is stolen, LifeLock helps make the recovery process as pain-free as possible, offering up to $25,000 in stolen funds reimbursement if you lose money due to identity theft. As a LifeLock member, you’ll also get help from U.S.-based restoration specialists who will personally handle your case and help you get back on your feet.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about.
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.







