What is card cloning?
Card cloning is a type of financial fraud where criminals copy stolen credit card data onto a blank card. Cloned cards can be used anywhere a regular card can, including in stores, at ATMs, or online, allowing criminals to spend or withdraw money from your account.
But fraudsters don’t have to use cloned cards in purchases to make money from their scheme. Some might instead sell cards they clone, or stolen card data that can be used to create cloned cards, on the dark web or private messaging apps like Telegram.
Some clone cards are generic, white cards, while others look exactly the same as standard credit cards. They can even look like gift cards, as two Florida criminals proved when they cloned credit card information onto Walmart gift cards. The only way to determine if such cards are fake is to compare the scanned number to the number on the card.
How does card cloning work?
Cybercriminals harvest credit card data using devices like skimmers and shimmers. The stolen data is sent to a computer or phone before cybercriminals use a cloning device to duplicate it onto a blank card. Then, they can use the newly created clone card like a regular one or sell it online.
Here’s a closer look at how the card cloning process works:
- Skimming devices harvest card data: Cybercriminals attach devices like card skimmers (which read the magnetic strip on a card) or shimmers (which read the microchip) to ATMs or payment terminals. They may also set up tiny cameras to record your PIN. Such devices can be very difficult to spot.
- The data is sent to criminals: Stolen card data harvested by skimmers is transferred to a cybercriminal’s phone, computer, or specialized device. Cybercriminals may compile databases of stolen card data for later use — since making purchases right away may tip off law enforcement about the skimmer’s location.
- Your card is cloned: Criminals use cloning devices to copy the stolen data onto a new card. This may involve demagnetizers, which erase data from the magnetic strips of existing payment cards for use as new clone cards.
- Criminals use the card for purchases: Criminals can take a cloned card and use it just like the one in your wallet. If you don’t regularly monitor your transactions, you may not immediately notice this form of credit card fraud.


Card cloning methods
Card cloning commonly starts with magstripe skimming or card chip shimming. RFID skimming may also be used to steal card data, although some experts believe that this threat is remote.
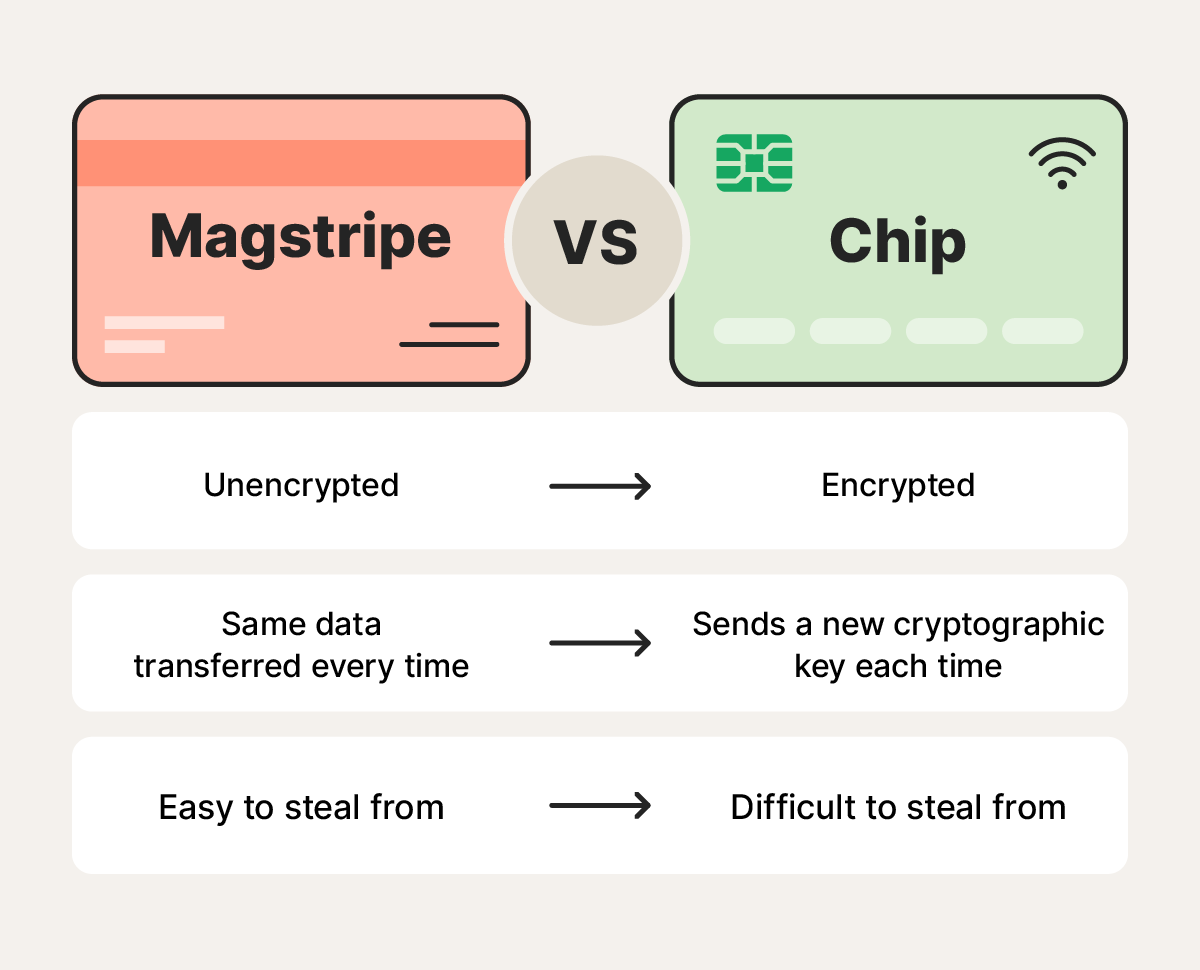
Magstripe skimming
Magstripe skimmers copy the data stored on the black magnetic stripe on the back of a card when it’s swiped. Criminals fit a thin skimming device on or inside an ATM, gas pump, or point-of-sale reader so the skimmer captures the card’s data as you swipe.
Magstripe cloners appeal to criminals because they rely on older, unencrypted technology. To address this, MasterCard plans on phasing out magnetic stripes by 2033.
Card shimming
Card shimming is a form of skimming that targets chip-and-PIN cards’ EMV chip. Criminals slip a thin, hard-to-see device, called a shim, inside an ATM’s card slot. The shim intercepts the chip’s data when you insert your card.
Chip-and-PIN cards remain relatively secure because they require both the chip and your PIN, but that protection only works if your PIN stays secret. Card shimming scammers might also install a small camera above the PIN pad, which is why it’s important to always cover the keypad when entering your PIN.

RFID skimming
RFID (radio frequency identification) or NFC (near field communication) skimming uses a concealed, portable reader to capture the short-range radio signal from a contactless card or phone that’s a few inches away.
They theoretically allow thieves to scan nearby cards without even touching them, especially in cramped environments like subway cars or concerts.
You can reduce risk by using tokenized wallets (like Apple Pay or Google Pay) for contactless payment and enabling transaction alerts and statement monitoring.
How to protect yourself from card cloning
You can help protect yourself against debit or credit card cloning by using contactless payment methods and sticking to bank ATMs. You should also avoid using cards with magstripe readers.
Here are some more tips on protecting yourself from card cloning devices:
- Stick to newer card tech: Contactless payment and EMV-based chip-and-PIN cards are more secure than payment methods that rely on magstripe. Avoid swiping credit cards to reduce the odds of your data being stolen.
- Check for card skimmers: Examine POS terminals and ATMs for loose plastic, glue, or tape. Avoid card readers that show any of these signs. However, keep in mind that ATMs may host a skimmer even if you don’t notice any signs of tampering.
- Use cash at sketchy locations: Avoid using ATMs or card readers in unsafe, remote locations. Isolated convenience stores in places with low police presence are more likely to be criminal targets.
- Stick to bank ATMs: Bank ATMs are more secure than third-party ATMs because they’re more likely to be monitored, especially if they’re indoors.
- Monitor your bank transactions: Many bank apps include monitoring features that let you track your transactions. Install your bank’s app and enable transaction alerts so you’re notified of suspicious charges.
- Shield your hand when entering your PIN: Use your hand to shield your PIN from shoulder-surfing criminals and hidden cameras that might steal your PIN. Place your hand as close to the PIN pad as possible, covering all angles.
- Get an RFID-blocking wallet: RFID-blocking wallets may help stop contactless payment skimmers from stealing your information, although the jury is still out on whether RFID skimming is a real threat, with some experts calling RFID crime “really rare.”
What to do if you’re a victim of a card cloning scam
If you realize your card might have been cloned, immediately report the issue to your bank to block the cloned card and order a new one. Then, notify your local police department and place a fraud alert. Monitor your accounts to ensure no additional information was leaked.
Here’s what you should do to mitigate the risk of serious losses if your debit or credit card is cloned:
- Report the issue to your bank: Inform your bank about the cloned card and order a new one. You can also place a fraud alert, which will notify the credit bureaus that you’re vulnerable to fraud, helping reduce the risk of the fraudster opening new accounts in your name.
- Dispute unauthorized charges: Review your account’s transaction history and write down charges you don’t recognize. Discuss these charges with a bank representative on the phone or submit an online fraud dispute via your bank’s website.
- Notify your local law enforcement: Call your police department’s non-emergency line and make a report. The police report will help you dispute bank transactions and other potential fraud later.
- Report the incident to the FTC and IC3: Report the incident to both the Federal Trade Commission (FTC) and the Federal Bureau of Investigation’s Internet Crimes Complaint Center (IC3).
- Monitor your accounts: Criminals will often re-target individuals who are the victims of stolen information. Monitoring your credit and bank accounts will help you determine if you’ve become the long-term target of a criminal.
Can cloned cards be traced?
Cloned cards may be traced using transaction metadata (like the merchant, terminal ID, timestamps), CCTV, and digital clues like IP addresses or device fingerprints, but that information rarely pins down a culprit without additional evidence.
Tracing a cloned card becomes even more difficult when criminals transfer the money from the cloned card to a prepaid one. Some criminals may also rely on money mules, intermediaries tasked with moving money to shield the criminal’s identity.
Can the bank find out who used my card?
While banks can usually see where and how a card was used, linking a transaction to a specific person typically needs extra evidence such as CCTV footage, merchant records, or law-enforcement subpoenas. Transaction data alone often doesn’t identify the criminal.
Defend yourself from card cloning attacks
Your card being cloned can leave you feeling overwhelmed and vulnerable. But you can safeguard against the potential fallout of card cloning attacks by subscribing to LifeLock, with credit monitoring helping you spot signs of credit fraud. You’ll also get stolen wallet protection, 24/7 live member support, and a reimbursement package of up to $1 million if your identity is stolen.
FAQs
Are clone cards illegal?
Yes. Creating, possessing, or using cloned payment cards is illegal and is routinely prosecuted as credit card fraud. Penalties can include prison terms or large fines.
Can a cloned card be used at an ATM?
Yes. ATMs don’t recognize the difference between a cloned card and a legitimate one. If a criminal clones your card, they can use it to withdraw money from an ATM — until you notice weird transactions and block the card that was cloned.
Do the police investigate card theft under $500?
The police may not investigate credit card theft under $500, preferring to allocate limited resources to other priorities. But, if you have evidence pointing them to the perpetrator, they may be more likely to investigate the crime. Either way, you should still report the incident as it can help you evidence fraudulent transactions in later disputes.
Editor’s note: Our articles provide educational information. LifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about.
Start your protection,
enroll in minutes.
LifeLock is part of Gen – a global company with a family of trusted brands.
Copyright © 2026 Gen Digital Inc. All rights reserved. Gen trademarks or registered trademarks are property of Gen Digital Inc. or its affiliates. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.







